Our Blog
03-24-2021
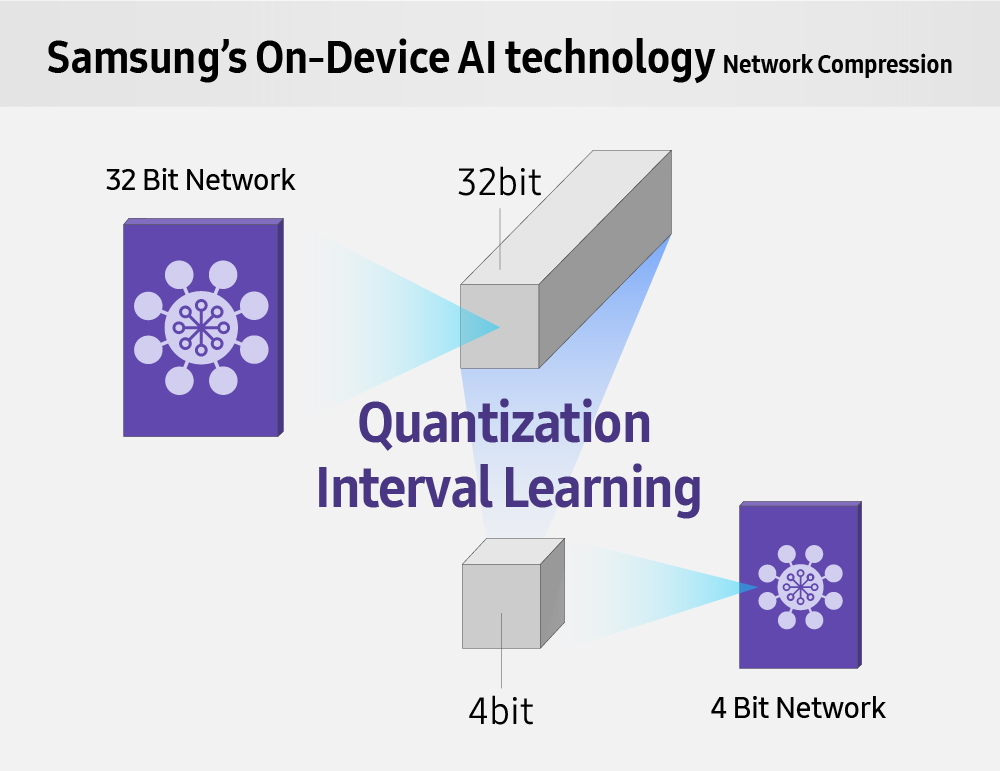
This series of blogposts aims to describe and explain the internals of a recent addition to Samsung's system-on-chips, namely their Neural Processing Unit.
02-03-2021
Exploring Aarch64 sidechannels on Android, with VDSO as a potential KASLR oracle
01-04-2021
A deep dive into Samsung's RKP security technology, covering a bonus bug that would allow EL1->EL2 privilege escalation which was patched.
12-20-2020
In this post, we discuss how to exploit an Android Linux Kernel LPE in the binder subsystem.
While reviewing attack surfaces on iOS for potential sandbox escapes, we uncovered a critical flaw in a custom Off-The-Record implementation relied upon by iCloud Keychain Sync in addition to a memory trespass error (CVE-2017–2451). The flaws were reported and addressed in one of Apple’s latest security updates. We are currently not aware of any additional uses of the custom OTR implementation.
About two years ago, Eduardo Vela pointed out that the Navigator Beacon API can be used to exploit "accidentally-CSRF safe" websites. Philip Olausson and I recently noticed Chrome 59, which just shipped, addressed this behavior and we investigated a Flash bypass.
At Longterm Security, we provide training for organizations looking to build up or improve their in-house Security Operations capabilities. Our other trainings include offensive security training which focuses on reverse engineering, vulnerability discovery, and bypassing exploit mitigations.We also have defensive security training for security design reviews, secure coding and testing methodology.
Over the years there have been numerous high-profile attacks that have compromised accounts hosted on Google Mail or the G Suite. There are some highly effective measures that can be taken to help prevent these scenarios. And the most important tip is probably…